Blog
CATEGORY: Data Protection
Multi-factor Authentication (MFA): What is it and why you need it
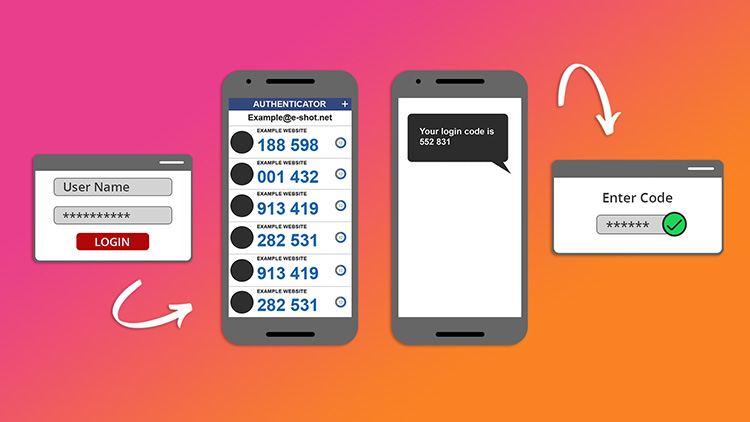
Traditional usernames and passwords can be easily compromised. Multi-factor authentication (MFA), is a security control that requires users to verify their identities by providing multiple pieces of evidence before gaining access to a device or application. It is an enhancement over the two-factor authentication (2FA), which requires only two pieces of evidence. This is the only difference between the two. A few examples of multi-factor authentication are codes created by Authenticator apps on mobile devices, answers to personal security questions, codes sent to an email address or by SMS to a phone, fingerprints, etc.
And why is it important?
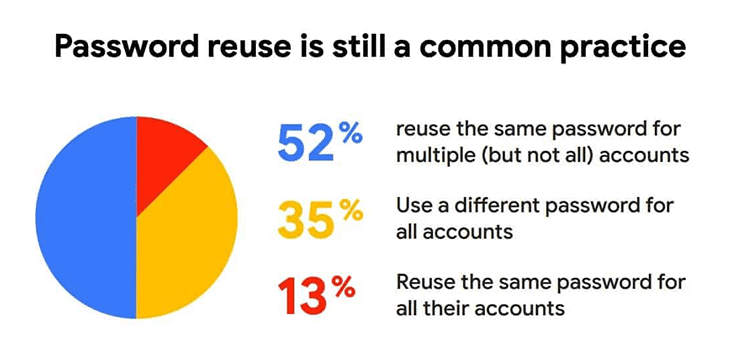
According to entrepreneur 90 percent of employee passwords can be cracked in six hours and 65% of people use the same password is multiple places.
Whereas Microsoft manager Alex Weinert stated in a 2019 blog post that, “Based on our studies, your account is more than 99.9% less likely to be compromised if you use MFA.”
Why a second line of defence is essential
For a more recent example of where MFA would have prevented a major incident we need only to look to May 2021. A Russian-based hacker-group known as Nobelium managed to access a cloud marketing service before launching a phishing campaign that breached 3,000 email accounts across 150 organisations.
Nobelium gaining access to the Constant Contact account of the United States Agency for International Development, or USAID. With access to the Constant Contact email service through a USAID account, Nobelium was able to “distribute phishing emails that looked authentic but included a link that, when clicked, inserted a malicious file used to distribute a backdoor” called NativeZone. “This backdoor could enable a wide range of activities from stealing data to infecting other computers on a network,” wrote Tom Burt, Microsoft’s corporate vice president of customer security and trust.
This serves as a powerful lesson for any organisation that is in a position of trust, account credentials need to be protected as cyber-crime actors will exploit any opportunity to achieve success for their activities. But regardless of how strong you think your password is (NCSC off brilliant advice on strengthening your password) the more layers of protection you have the harder. Cloud or not, cyber-attackers will continue to target identities, because they provide access to on-premise systems as well as cloud services.
We are taking proactive approach to safeguard our technology infrastructure and protect our clients from the increasing threat of cyber-attacks and would strongly encourage you and your team to enhance your personal security practices as well.
What are the possible authentication factors?
Something that you know – This could be a password, a PIN code or answer to a secret question
Something that you have – This is always related to a physical device, such as a mobile phone, a USB security device (YubiKey), a security code generator, etc.
Something that you are – This is a biological factor, such as a face or voice recognition, fingerprint scanner, DNA, handwriting or retina scan
Time and location factors identifying your physical location. For example, attempt to log into an account from an unauthorised country can be blocked or a time sensitive access.
Most common forms of 2FA
A one-time password, that you receive as text message (SMS) on your mobile phone
The security code generator device, which generates a specific code at a specific time – usually used with your username and password for Internet banking
The security code generator mobile app generates a random time sensitive code.
Here are a few examples of security code generating mobile apps:
Google Authenticator available for Android, iOS and Blackberry
LastPass authenticator available for Android, iOS
Authy for Android, iOS, but also available as desktop app and browser extension
HMRC authenticator
These apps use Time-Based One-Time Password (TOTP) algorithm. They will generate a time-sensitive six-digit code, which you can use to verify your login. The code will typically refresh every 30-60 seconds.
The latest advice from Microsoft is NOT to use MFA with SMS or Voice
Microsoft warns against SMS, voice calls for multi-factor authentication: Try something that can't be SIM swapped.
Sending codes over the insecure public telephone network isn't the way to go
Watch our 2FA video
Created in partnership with South East Region Organised Crime Unit (SEROCU)

Take a look at our help article to set up 2FA on your e-shot account.
Updated: March 2022
Solutions
Email marketing healthcheck
We are confident that we can help you, which is why we offer a free healthcheck to identify potential issues with your current programme and free advice on things that could be done to improve it.

.jpg)